A recent study shows that 56% of IT departments report an increase in their response time for cyberattacks. These actions tend to go against our better judgment and defy common sense. From the cost of a malware attack to the percentage of security training misses annually.
. ( Verizon, 2019) Ask questions Additionally, about a third (33 percent) reported using the same password for work and personal devices, and just over a third (35 percent) said they had clicked on an email link from an unknown sender. The five books that Chris has written has lead to our company being engaged by organizations from all industries in the US with the goal of uncovering, patching and mitigating social engineering vectors. They are a type of computer hacking in which the attacker can obtain information such as usernames, passwords, and credit card details by deceiving users into giving the information away. 59% of companies experienced malicious code and botnets and 51% experienced denial of service attacks. It is also in our resources page. Or, the message may come from someone who wants to friend you on a dating or social networking site. Social engineering is a practice that is as old as time. Utopia P2P As Part of the Alt-tech Movement, The Best Chatting Messenger: Threema vs Signal vs Utopia, Crypton (CRP) Next Big Cryptocurrency for 2023, Google Notifies Users If Someone is Looking For Personal Data. Contact us for more information on our Anti-Phishing Solutions or Cyber Security Training for employees. After Microsoft is DHL, with about 18% of cybercrimes, as well as companies such as PayPal, LinkedIn, Google, and Chase. Baits are very attractive and enticing, not to mention manipulative, and their end goal is to infect your . Social engineers also pretend to be employees calling from an outside phone line. However, the most common targets are neither CEOs nor people in IT.
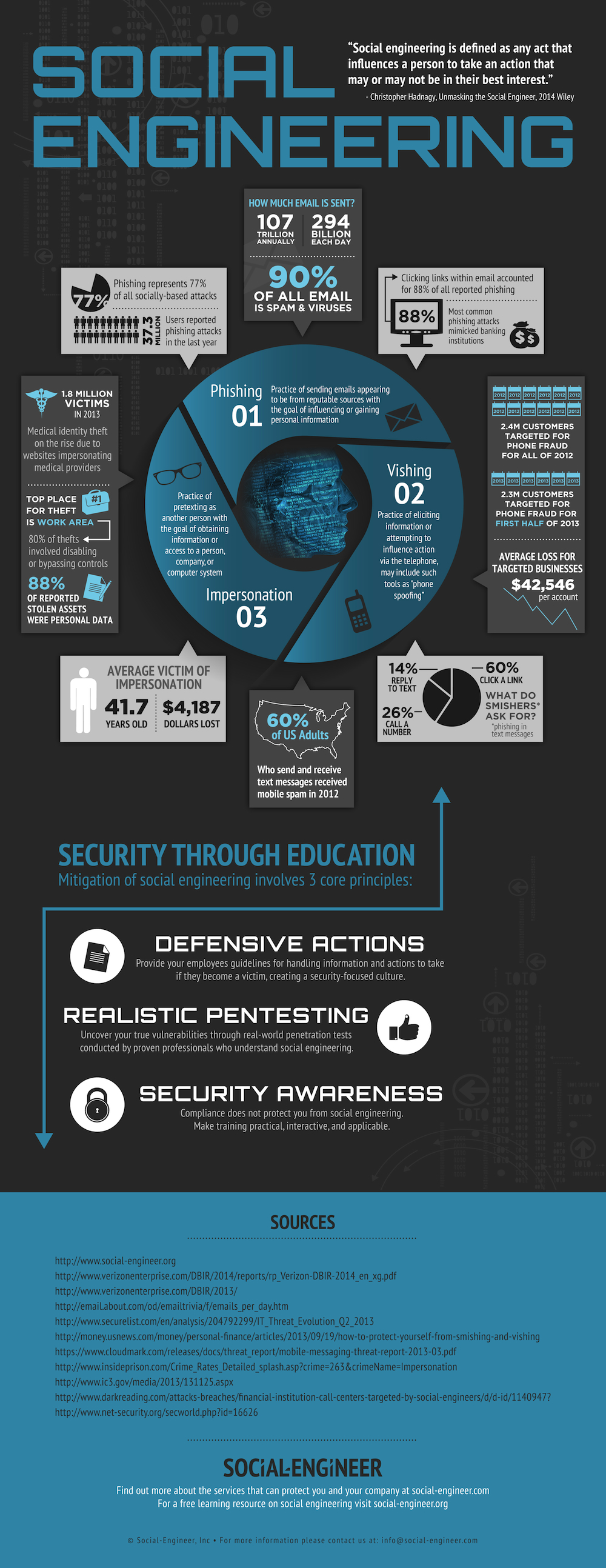
Plus, the World Economic Forum's 2020 Global Risk Report states that the rate of detection (or prosecution) is as low . National Center for Science and Engineering Statistics Directorate for Social, Behavioral and Economic Sciences National Science Foundation 2415 Eisenhower Avenue, Suite W14200 Alexandria, VA 22314 Tel: (703) 292-8780 FIRS: (800) 877-8339 TDD: (800) 281-8749 E-mail: ncsesweb@nsf.gov. Get in touch today to schedule one of our staff to speak at your event. Social Engineering Statistics 98% of cyberattacks rely on social engineering. What are social engineering attacks? The planning process required certified engineering design drawings associated with design life, durability and suitability of materials, and baseline ecological . Clearly, this is a growing problem. A few examples that come to mind are the 2017 Equifax Breach (which affected nearly 150 million consumers), the 2020 Marriott Breach (which impacted 5.2 million guests), and the Twitter Breach (which targeted 130 accounts in 2020). Revenue from scamming skyrocketed by a whopping 82% in 2021. If you follow our Twitter (@SocEngineerInc, @humanhacker), youll see the stories. It uses psychological manipulation to trick users into making security mistakes or giving away sensitive information. Explore our eBook with key recommendations, You need to know these 10 cyber security statistics. Unfortunately one of the biggest spoofs going I.e. Privacy Policy, 90% of the people we ask will provide not just the spelling of their names but their email addresses without confirming our identity, 67% of the people we ask will give out social security numbers, birth dates or employee numbers, We have a 100% success ratio in physical breaches. But you can prevent that from happening. Copyright 2022 Social Engineer, LLC. View our infographic for statistics around common social engineering tactics and recommendations on how to avoid falling victim to social engineering attacks! Thats just considering the money and data that the average company loses. Social Engineering Attacks Statistics continue to show social engineering playing a part in a vast number of breaches. According to a 2014 report by Enterprise Management Associates (EMA), more than 55 percent of a companys personnel, excluding security and information technology staff, have not received security awareness training from their organizations. Purplesec, 4. We at Web Tribunal thought wed give you some tips on how to protect yourself from social engineering frauds: If the social engineering statistics that we just covered prove anything, its that social engineering is a threat to millions of companies and individuals around the globe. They can also use script files (11%) or compressed files (4%), but executable files are preferable because the program starts the moment you open it. About 1% are phone attacks. Of, if the message is from a stranger, ignore it and delete the message, or check it out on a search engine (do a quick search for commonly used phrases indicating scams) before responding. As mentioned in the blog, Phishing and Vishing are on the rise. For example, cybercriminals pretended to be government agents who needed your personal information to sign you up for financial support or early vaccination. People think, "Hey, he looks and acts like me, so he must be one of us.". DHL comes in the second position, with 18% of cybercriminals using the brand name. In more than 70% of cases, all files sent by malicious hackers to emails include Windows file attachments. Van Marken suggested that specialists were needed to attend to human challenges in addition to technical . Policy, 17+ Sinister Social Engineering Statistics for 2022. Check out what these statistics mean, where social engineering fits in and how you can protect your business or agency from cyber attacks. Its no secret that in recent years, cybercriminals have improved their methods of data theft, and with their help gigabytes of confidential information are leaked daily. Cybersecurity and social engineering awareness campaigns brought the 30% fail rate down to around 5%. The same report indicates that new employees are the most susceptible: 60% of IT professionals cited recent hires as at high risk of falling for social engineering tactics. ESET Threat Report, 9. Does it constitute fraud and sorry about your luck. Cybercriminals can target any individual or company, though statistics show that healthcare institutions, government agencies, and universities are the preferred targets for social engineering scams because of the information they store. Cybercriminals manipulate technologies to steal data but how exactly do they trick people into divulging sensitive personal information? Do not download attachments and do not follow suspicious links in emails received even from people you know. In fact, recent security studies suggest that just one percent of employees are responsible for 75 percent of enterprise security risks. If you find the email suspicious, verify the mail with the sender right away. 16. $43 billion stolen through Business Email Compromise since 2016, reports FBI Process, Privacy Over time, social engineering attacks have grown increasingly sophisticated. Be suspicious of all unknown callers That is why Social-Engineer decided to fund the creation of an intensive and extensive infographic. Now factor in how common cyberattacks are (internet privacy stats say one occurs every 39 seconds) and it should come as no surprise that experts predict the global annual cost of cybercrime will reach an astronomical $10.5 trillion by 2025. Cybercriminals who use social engineering lure you to share your personal information, open infectious files, or give them access to restricted data. 1. Sophisticated phishing scams have been known to use information about your networks and position through LinkedIn or Facebook to gain just enough details about you to seem plausible, or pique your curiosity. Although there are some (21% if we consider both current and former employees) who may intentionally use social engineering hacks to get back at you. Be Aware of your surroundings Thanks to them, the databases on the internets dark side are replenished at a rapid pace every year. In computing, social engineering refers to the methods cybercriminals use to get victims to take some sort of questionable action, often involving a breach of security, the sending of money, or giving up private information. Social engineering is the most common technique deployed by criminals, adversaries,. Other often impersonated brands are PayPal, LinkedIn, Google, and Chase. Learn how Mimecast email security solutions help to keep your company safe.Read More. Read more here. Social engineers can wear a similar-looking uniform, make a fake ID badge, or simply dress like real employees. In your online interactions, consider the cause of these emotional triggers before acting on them. With shocking statistics like "61% of electronics reviews on Amazon being fake," AI can have a huge impact to help filter out these misleading reviews. Threat actors form relationships with targeted victims to get access to information or personal details that can be used to breach corporate networks, facilities, or accounts. However, if organizations are taking appropriate security measures, such as deploying a security suite like SIEM or/and SOAR, then the chances of survival are to a large extent. The latest phishing statistics reveal that the FBI registered 241,342 attacks in 2020, compared to 114,702 in 2019. Statistics around Social Engineering Over 400 businesses are targeted by spear-phishing scams everyday. 90% of data breaches have social engineering components to them. Social engineering, by definition, takes many different forms, including phishing (and its offshoots), sweet-talking or lying, tailgating, threats and intimidation, and other tactics. We must pay more attention to the emails we send and receive! Zero minus zero still equals zero. Only personal vigilance and a critical approach will allow you to recognize the threat of social engineering and signs of manipulation of your actions. The only difficulty is to find the right approach for each person, although professional social engineering people almost always act impromptu, relying only on their feelings. COVID-19 also impacted companies ability to face cybersecurity threats. Types and Applications of Biometric Technology, 20 Facial Recognition Statistics to Scan Through in 2022, 19 Internet Privacy Statistics to Be Paranoid About in 2022, Identity Theft Statistics to Snatch in 2022, APPS 90% of data breaches have social engineering components to them. Read about a famous email scam and be ready to protect yourself. Unaware that life beyond the internet exists, Nick is poking servers and control panels, playing with WordPress add-ons, and helping people get the hosting that suits them. Israel came in second place with 15.24%, followed by France (12.58%) and Brazil (11.86%). Social engineering is the term used for a broad range of malicious activities accomplished through human interactions. Be careful about what information you share with a stranger over email, or what information you put about yourself on social media.
On average, social engineering attacks cost $130,000 The term social engineering refers to personalised psychological manipulation and tactics that leverage your trust in order to steal data or hack into your network or device. That is why Social-Engineer decided to fund the creation of an intensive and extensive infographic. Social engineering emails usually impersonate a well-known company to increase the chances of you opening them. Microsoft, whose services are used by more than one billion people all over the world, is most often used as a trick to lull the vigilance of internet users. When you receive something like this in email form, it is called spear phishing. AI is also used to catch malware, help with intrusion detection, aid red team hackers and numerous other aspects of cybersecurity. 67% of the people we ask will give out social security numbers, birth dates or employee numbers We have a 100% success ratio in physical breaches How do these numbers compare to the market around the globe? 98% of Cyber Attacks Involve Some Form of Social Engineering In the broad world of cyber attacks, 98% involve social engineering on some level. In 2020, 75% of companies reported being victims of phishing. The Doctoral Program in Social and Engineering Systems (SES) offered by the Institute for Data, Systems, and Society is a unique research program focused on addressing concrete and societally significant problems by combining methods from computing, data science and statistics, engineering, and the social sciences. Download PDF - Engineering Statistics, 5th Edition [PDF] [145k4u227k60]. GlobalSign, 5. Phishing attacks present the following common characteristics: Undoubtedly, social engineering attacks are very dangerous and can have serious consequences for organizations in 2020. 62% of all businesses experience social engineering attacks in 2018 Why Is Cyber Security Training Important? These are all, Anonymous P2P messaging is a special peer-to-peer chat that provides users with privacy and security of their transmitted data. In simple words, with the knowledge and techniques of social engineering, you can easily get a person to do exactly what you need. Social Engineering Attack Detection Model (SEADM) is a quick and effective way to determine if an requester is trying to manipulate an individual into disclosing information to which the requester does not have authorization for. Please take a quick look, and if you like it, pass it on to someone you know. Knowbe4, 15. While bad actors have many techniques for attacks at their disposal, social engineering is still one of the most effective means of compromise. GetApp's 2022 Data Security ReportSeven Startling Statistics. If we are talking about a company, then all employees should be warned about the danger of disclosing personal information and confidential information of the company and ways to prevent data leakage. Rather than attempting to use brute force to bypass a network's existing cybersecurity defenses, cybercriminals deploying social engineering strategies attempt to prey on unsuspecting . However, the opposite is true for vishing34% of employees in the 18-22 age group know what vishing is, whereas just 20% of employees who are older than 55 are familiar with the term. Social Engineering relies heavily on the six Principles of Influence established by Robert Cialdini, a behavioral psychologist, and author of Influence: The Psychology of Persuasion. It works because hackers and bad actors know how to manipulate us and trick us into clicking malicious links. We can remember a time when typing that into a search engine lead to almost no return. Human-based attacks in the form of phishing, vishing, and impersonation are on the rise. With 241,342 successful incidents, phishing was the most common cybercrime in 2020 in the US. Social engineering is a burning issue because it exploits peoples natural tendency to trust others and tricks them into revealing sensitive information. Lets agree that hacking a database is much more difficult than just deceiving a person who has access to all the necessary data. Social engineering (security) In the context of information security, social engineering is the psychological manipulation of people into performing actions or divulging confidential information. Social engineering is used in 98% of cyberattacks. As of Jan 17, 2021, the search engine powerhouse, Google recorded 2,145,013 phishing sites. Its easier to fool people rather than to infiltrate a secure computer system, so its no surprise that about 70% to 90% of all data infiltration is due to phishing and social engineering attacks. According to PurpleSec (2021), 98% of cyberattacks rely on social engineering. It is often easier to fool someone into giving away their password to get access to a corporate network than it is for them to get in via hacking. A phishing email tricks individuals into taking action immediately. Cyber criminals know that people are often the gateway to valuable credentials and databases or account details. Social engineering scams stole over $5 billion worldwide from 2013-2016. Interesting, phishing attacks account for the first attack vector of nearly 1 in 3 of all cyberattacks. Lock your computer when you leave your workplace. These scams try to catch you off guard, leveraging fear, curiosity,habit and innate trust against you. 1. We hope you enjoy it and find it extremely useful. What Are Biometrics? Social engineering is the skill or art of manipulating individuals into giving up sensitive information. This piece of research gives a briefing . The largest underwater sculpture in the world, the 'Coral Greenhouse' by artist Jason deCaires Taylor, was commissioned by the Museum of Underwater Art and installed at John Brewer Reef, Australia, in December 2019. Despite spending millions of dollars on state-of-the-art perimeter and end-point security controls, determined actors are still finding their way inside company networks every day by exploiting the human factor. Lets take a quick look at these stats to see the staggering impact social engineering has around the globe. INFOTECH, 19. Therefore, they unknowingly open access to data for fraudsters. | All Rights Reserved. If a cybercriminal introduces himself as a representative of a well-known company, then his credibility with an ordinary person increases several times. Use password managers. These social engineering statistics prove why we should pay more attention to the people we give our information to. As reported by First Orion, phone scammers were able to get 270% more personal information in 2020 than they did in 2019. It works by taking advantage of our natural curiosity. Unfortunately, social engineering is one of the most dangerous forms of cybercrime. FINANCES, BUSINESS & All Rights Reserved. As always, our motto is Security Through Education and we wanted to make the infographic about that, so it is complete with three principles to help you, your families, and your companies stay protected from social engineering threats. Social engineering refers to the practice of using non-technical methods to trick people into doing something they wouldnt normally do otherwise. Dont trust caller ID Unlike, Paradoxically, despite the variety of messengers now available, people usually dont have to choose between them they just use, Stay up date with useful tips, tricks and latest news.